The Tool ISP’s use to track down hackers.
 If your network is under attack, how can you know who’s attacking you? Even if you know what part of the Internet the attack is coming from, what can you do about it? Who can you call to make it stop? We’re going to look at one of the most powerful tools in your arsenal for identifying where traffic is coming from and who owns the network. The tool is whois.
If your network is under attack, how can you know who’s attacking you? Even if you know what part of the Internet the attack is coming from, what can you do about it? Who can you call to make it stop? We’re going to look at one of the most powerful tools in your arsenal for identifying where traffic is coming from and who owns the network. The tool is whois.
Talking about whois sounds like the beginning of the Abbot & Costello “Who’s on First” skit. COSTELLO: “What is whois for?” ABBOTT: “whois on First. What is on second…” But learning about whois enables you to query some of the most important underpinnings of the Internet.
The core of the Internet is a complex relationship between Telecommunications companies, quasi-government entities and non-profit bureaucracies with lengthy acronyms like ARIN, IANA, and the like. It’s these relationships that define how packets of data are moved and routed around the world.
whois allows you to see these relationships and uncover the humans and organizations behind these movements. This means knowing who you can contact when the Internet is not working or if malevolent entities are using the Internet to mount attacks against your clients. In this article we’re going to take a deep dive into whois and reveal its power.
Versions of whois
whois refers to both a program and a protocol. The program communicates over the Internet to a server that manages a database. The query protocol between the program and server is also referred to as whois (https://tools.ietf.org/html/rfc3912). In this article, we are not interested in the protocol, but will focus on the program.
There are several versions of the whois program. Most UNIX platforms come with the RIPE whois installed by default. For Windows platforms, we recommend you download the RIPE client from Cygwin (http://cygwin.org). After you install cygwin, add it to your path to make following along with the examples in this article simpler.
What’s on second?
Speaking generally, there are two broad classes of questions you can answer using whois: questions about who owns a domain and questions about who owns a network. The whois client attempts to figure out the type of question you are asking and directs the question to the appropriate server, but you can override this and force whois to query a specific server.
In this article, we’re not interested in querying domains and instead focus on network queries. Network ownership and management details are delegated to five Regional Internet Registrars (RIR). Each is assigned a specific portion of the world and each runs their own whois for servers for answering your questions.
The five RIR’s and their servers are:
| RIR | Region | Server |
|---|---|---|
| ARIN | North America | whois.arin.net |
| LACNIC | Central & South America | whois.lacnic.net |
| RIPE | Europe & Central Asio | whois.ripe.net |
| APNIC | Asia Pacific & Australia | whois.apnic.net |
| AFRINIC | Africa | whois.afrinic.net |
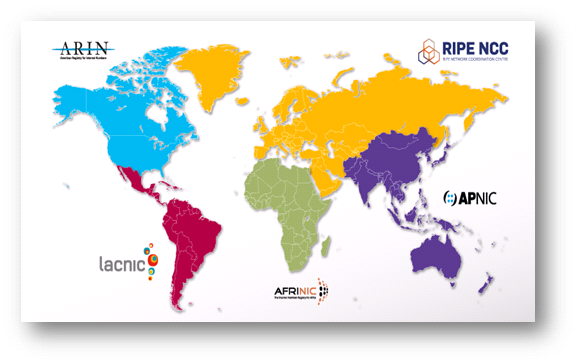
Source: https://www.nro.net/about-the-nro/regional-internet-registries
How to ask a question
Most of the time, using whois is a simple matter of typing your question on the command line. whois will try to make sense of the question and handle forwarding it to an appropriate server. If the server whois first contacts doesn’t know the answer, it returns a referral and whois resubmits the question to the referral server and so on until it gets a reasonable answer.
Here’s a sample:$ whois 8.8.8.8
This query is asking who owns the ip address 8.8.8.8.
whois will respond with a large block of formatted text. The text starts with some boilerplate about terms of use. The answer to the question follows. It will look something like:
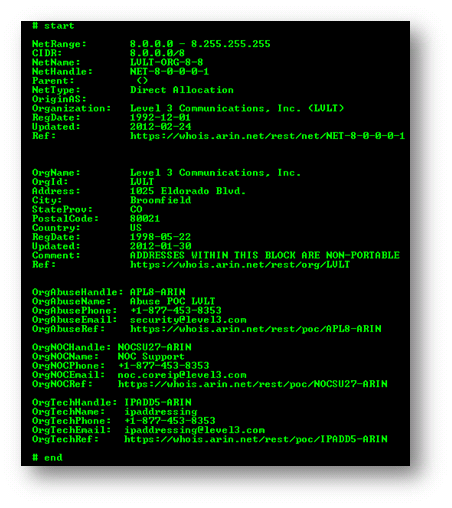
The text is fairly self explanatory. When the response comes from ARIN (as this answer did), the responses are broken into sections with each section separated by the tags ‘# start’ and ‘# end’.
In this response, the first section identifies the address as part of a larger /8 CIDR block owned by Level(3) Communications. It also provides three different contacts for Level(3): their security department, their network operations center, and their ip addressing department. The contacts include email addresses and phone numbers that can be a real life saver if you’re under attack.
So far so good. But if you look closely at the text block, you’ll notice there is another set of “# start” and “# end” tags. This provides the following additional details:
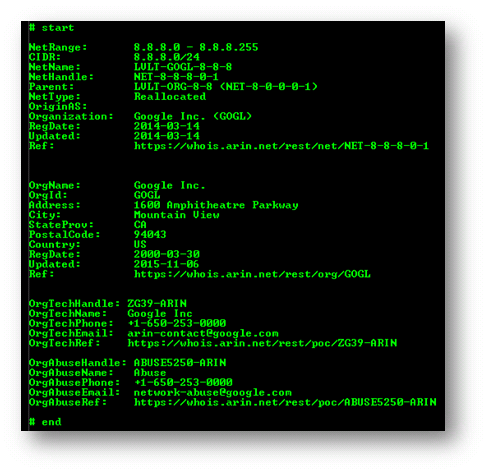
The server that responded to your query recognized the 8.8.8.8 address was part of a delegation made by Level(3) to Google. It is Google that actually owns the address you asked about. The server therefore responded with a second start/end block that provided additional information.
The server provided the refined network details and two contacts for Google: their technical contact and abuse department. You now have the phone number of Google’s abuse department which you could contact if the 8.8.8.8 address was attacking your network.
There’s another piece of information you can glean from the two response blocks. Knowing the fact that Level(3) owns the /8 and Google has a delegation from them, you can draw the conclusion that Google is buying Internet access from Level(3). This kind of architectural details can help you paint a mental picture of who is connected to who and how the Internet is put together.
Real world Queries
Let’s look at a real world use of whois. On the afternoon of December 19, the address 118.40.58.167 was used to scan a client’s network for open Telnet services. This is a common reconnaissance activity to locate target servers susceptible to brute force password guessing.
The simplest technique to confront this attack is to block the address. A quick firewall rule can be created to block the address. But what if hackers were using a number of addresses around the address? One could methodically and incrementally wait for each new address to be used and then add another firewall rule.
Ideally it is better to identify the network where the attack was originating and block that network. Then submit an abuse report to the owning ISP. This is a perfect task for whois. A quick check of `whois 118.40.58.167` revealed the following picture.
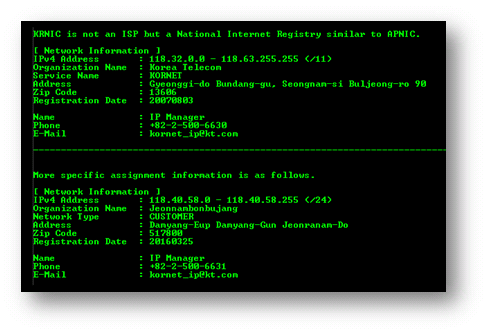
The response came from KRNIC, the Korea Internet & Security Agency which is the Ministry of Science, ICT, and Future Planning’s sub-organization dealing with the allocation and maintenance of South Korea’s IPv4/IPv6 address space. The KRNIC whois server separates response sections differently than ARIN. They separate sections with a dashed line.
You can see the ip address is assigned to Korea Telecom and part of the CIDR block, 118.32.0.0/11. You could block this entire CIDR range, but that would firewall off 2 million servers. That could be too broad a range for your client. If your client does any business in that part of the world, your firewall rule could interfere with their business activity.
The second part of the whois report shows the address is further broken down and delegated to a customer of Korea Telecom in South Korea. This customer has the CIDR block 118.40.58.0/24 that is a more reasonably sized network to firewall until you report the abuse to Korea Telecom.
How to report abuse?
After firewalling the network that is attacking your client, you need to decide if you want to report the abuse to the network owner. If the attack originates within the United States, reporting the attack is always a good idea. If it’s from overseas, you may want to consider whether reporting the attack may be information that gets passed on to the hackers to aid in their reconnaissance activity.
If you decide to report the attack, you can either call the telephone number you retrieved from the whois database or send an email. We recommend an email as it’s usually faster and you don’t need to be concerned about the business hours of the number you call. The only time to prefer a phone call is to remediate high impact events significantly affecting your client’s network.
When reporting abuse to a network owner, include the following details:
• The date and time the event occurred including the time zone
• What the attacker was doing
• Any documentation or log records to backup the report
• Contact information the network owner can use for followup questions
Here is a sample email used to report the incident to Korea Telephone
From: support@example.com
To: kornet_ip@kt.com
Subject: Your customer ‘Jeonnambonbujang’ is engaging in hackingA customer of yours is engaged in hacking activity. This whois database shows the ip address 118.40.58.167 is assigned to your customer
Jeonnambonbujang
Damyang-Eup Damyang-Gun Jeonranam-Do, 517800On December 19th, 2016, from 17:10 (EST) through 17:57, we detected seven (7) instances of your client probing the Internet for Telnet services. This is an unauthorized activity. This activity is continuing.
Your client may in fact have been infected with malware and it is this malware that is performing this scan without their knowledge. Please take the appropriate action to stop this activity from your client.
Below is a small sample of the incidents record on an intervening firewall. The format of the report is iptables:
Dec 19 17:10:36 SRC=118.40.58.167 LEN=40 TOS=08 PREC=0x20 TTL=43 ID=24548 PROTO=TCP SPT=11390 DPT=23 SEQ=3431844698 ACK=0 WINDOW=342 SYN URGP=0 MARK=0
Dec 19 17:14:09 SRC=118.40.58.167 LEN=40 TOS=08 PREC=0x20 TTL=43 ID=35766 PROTO=TCP SPT=11390 DPT=23 SEQ=3626766365 ACK=0 WINDOW=342 SYN URGP=0 MARK=0
Dec 19 17:20:56 SRC=118.40.58.167 LEN=40 TOS=08 PREC=0x20 TTL=43 ID=47453 PROTO=TCP SPT=11390 DPT=23 SEQ=3431844187 ACK=0 WINDOW=342 SYN URGP=0 MARK=0
You may reply to this email with any followup questions or comments.
Summary
whois is an incredibly powerful tool for investigating security incidents. You’ll find it useful to track and stop the source of network abuse or even spam. You can read more about whois on ARIN’s website at https://www.arin.net/resources/services/whois_guide.html .
Carroll-Net was founded in 1994 with the singular goal of providing datacenter services our clients require at a price they can afford, delivered everywhere they need them. The industry now calls this cloud services — we call it common sense.
You might like some of our other articles…
 Red Hat Bare Metal Backups |  Red Hat Dynamic Routing |  Red Hat Traffic Shaping |  Image vs. File Backups |
